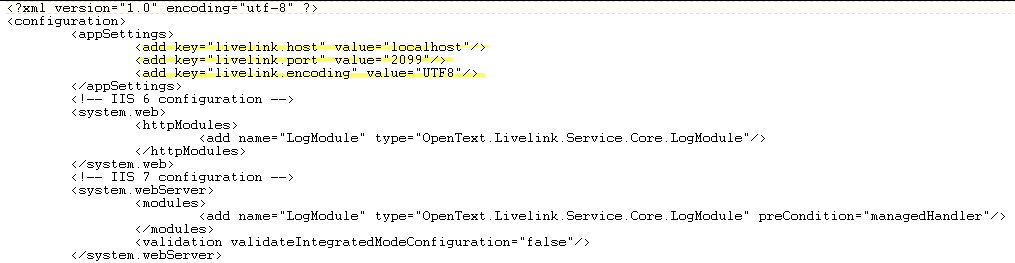
One of the nicest things in the content server area is, you can set Access Control Lists not only for the owner or the default group of a node, and you can add or revoke rights to the node for virtually all users and groups defined in the content server.
Here, we want do discuss how to do this using Content Server Web services. First, let’s see how ACLs are organized. A simple object would display something like this:
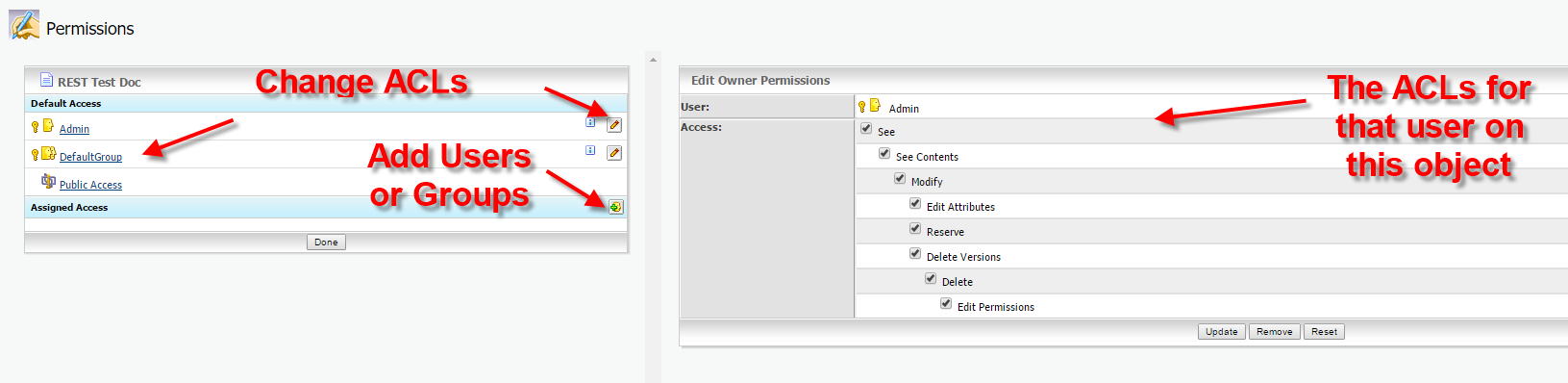
On the left hand side, you see the default access, there is always one Owner, one default group and a public group.
If you want to assign further access, you can select a user or a group by clicking on the bottom at the lower left hand side. This will select a user or a group. (Btw: It’s recommended to use groups instead of users)
On the right hand side, there are the ACLs for the selected user/group on the object. Here, we used the Administrator, therefore all rights are switched on.
Ok, how to use this on a c# client?
First, the ACLs for a given user are called NodePermissions. Use them like this. Let’s say, this is utils.setNodeRights(….)
/// <summary>
/// Creates a Noderight Structure and returns it
/// </summary>
/// <param name="rights">"all" or see (see,seecontents)</param>
/// <param name="id">the member ID for this node rights</param>
/// <param name="type">Owner, Ownergroup, Public or ACL </param>
/// <returns></returns>
public DocumentManagement.NodeRight setNodeRights(string rights, long id, string type )
{
DocumentManagement.NodePermissions newPerm = new DocumentManagement.NodePermissions();
newPerm.SeeContentsPermission = true;
newPerm.SeePermission = true;
if (rights.Equals("all"))
{
newPerm.AddItemsPermission = true;
newPerm.DeletePermission = true;
newPerm.DeleteVersionsPermission = true;
newPerm.EditAttributesPermission = true;
newPerm.EditPermissionsPermission = true;
newPerm.ModifyPermission = true;
newPerm.ReservePermission = true;
}
DocumentManagement.NodeRight newRight = new DocumentManagement.NodeRight();
newRight.Permissions = newPerm;
newRight.RightID = id;
newRight.Type =type;
return newRight;
}
The Nodepermissions is simply a container with the single access rights set to true or false.
When the definition is finished, the NodePermissions must be encapsulated in a structure called NodeRight. This contains the ACLs defined and the user/group for the ACL. Use the id as long integer, this is the unique identifier of a user/group in the content server. You can use MemberServices to get this number, if you know the login-name.
Then, the system wants to know, which kind this user/group is. Use ACL, if these are additional users/groups, or use something like Owner, Ownergroup or Public, if the ACLs should belong to the predefined entities.
How to use this?
First, login to the Webservices.
Second. Get the node, onto which you want to set ACLs.
Thirth. Get the node rights
NodeRightsUtilities utils = new NodeRightsUtilities();
DocumentManagement.NodeRights nodeRights = docclient.GetNodeRights(ref otauth, pargs.nodenumber);
Console.WriteLine("Got Noderights ");
DocumentManagement.NodeRight[] nodesrights = nodeRights.ACLRights;
Forth. Set the ACLs for the standard entities (if needed). Define a NodeRight for every entity (user/group) you want to set. Define these 2 right groups.
// setup standard permissions for base ACL group
DocumentManagement.NodeRight newRightstandardGroup = utils.setNodeRights("see", standardGoupID, "ACL");
DocumentManagement.NodeRight newRightsmanagerGroup = utils.setNodeRights("all", managergroupID, "ACL");
Define a special right group
DocumentManagement.NodeRight newOwnerright = utils.setNodeRights("all", ownerID, "Owner");
nodeRights.OwnerRight = newOwnerright;
The nodesrights on a node can contain something or be null. First, lets check, if the thing is null.
if (nodesrights == null)
{
Console.WriteLine("Nodesrights not found- no external Users/groups assigned");
Console.WriteLine("Setting a group with rights see/seecontent");
DocumentManagement.NodeRight[] allrights = new DocumentManagement.NodeRight[2];
allrights[0] = newRightstandardGroup;
allrights[1] = newRightsmanagerGroup;
nodeRights.ACLRights = allrights;
docclient.SetNodeRights(ref otauth, pargs.nodenumber, nodeRights);
authClient.Close();
Console.WriteLine("All Rights and Groups set --- Finish");
return;
}
In this case we simply define a NodeRight array with two entries containing our new RightstandardGroup and our newRightmanagerGroup.
Let’s store them into our newly created array.
Let’s store this array in our nodeRights under ACLRights. This will change our copy of our structure which we downloaded before.
Next is simply a SetNodeRights with the nodenumber and the updated nodeRights array to write our changes back to the server.
If there are already entries, you should set them like this:
// Just display the first Entry of the first assigned Users/groups
DocumentManagement.NodeRight right = nodesrights[0];
DocumentManagement.NodePermissions nperms = right.Permissions;
// check, if we do habe the groups already set
int newLen = nodesrights.Length;
// copy rights into new longer Array
DocumentManagement.NodeRight[] allrights = new DocumentManagement.NodeRight[newLen+2];
for ( int i = 0; i < newLen;i++ )
{
allrights[i] = nodesrights[i];
}
allrights[newLen] = newRightsmanagerGroup;
allrights[newLen + 1] = newRightstandardGroup;
nodeRights.ACLRights = null;
nodeRights.ACLRights = allrights;
docclient.SetNodeRights(ref otauth, pargs.nodenumber, nodeRights);
Console.WriteLine("All Rights and Groups set --- Finish");
authClient.Close();
In this case, our nodesrights come from the nodeRights.ACLRights, because there are alredy entries.
Now, let’s do the same thing like we did on a new structure. But, we don’t want to delete existing entries, lets simply add our new RightstandardGroup and our newRightmanagerGroup to the ACLRights array.
One thing, if finished, first set the nodesRights.ACLRight to null and then fill it with the new extended ACL array.
Then do a SetNodeRights with the nodenumber and the updated nodeRights array to write our changes back to the server.
Finished. Quite easy, isn’t it?
BTW: There is no equivalent to do this on the REST api at the time of this post.